filter (computing)
What is a filter in computing?
The term filter in computing can mean a variety of things, depending on the technology or technical discipline in question. There are four distinct applications for filters in enterprise computing:
- computer applications and programs
- cybersecurity
- telecommunications
- multimedia applications
How are filters used in computer applications and programs?
In computer applications, a filter is a program or section of code that's designed to examine each input or output request for certain qualifying criteria and then process or forward it accordingly. A filter is passthrough code that takes input data, makes some specific decision about it and possibly transforms it, and passes it on to another program in a kind of pipeline. Usually, a filter doesn't do input/output operations on its own. Filters are sometimes used to remove or insert headers or control characters in data.
Filters are commonly used within web-based applications to narrow the user's list of choices to a more manageable and usable number. For example, a filter can use machine learning or artificial intelligence to remove choices in order to simplify tasks or eliminate inappropriate options. For example, when searching a list of available cars on a used car website, users can narrow their options to the make, model, year and price.
On the back end, the application filter is tied to a database that lists all used cars for sale along with various attributes of each car that can be used to narrow down the user's choices. When a filter is executed, the application makes a data set call to reference only those vehicles that meet the filtered requirements.
How are filters used in IT security?
The use of filters in cybersecurity tools and practices is quite common. The following are examples of security-centric filters:
- network firewalls
- web application firewalls
- antivirus and malware prevention tools
- content filters
- intrusion prevention systems
- access control lists
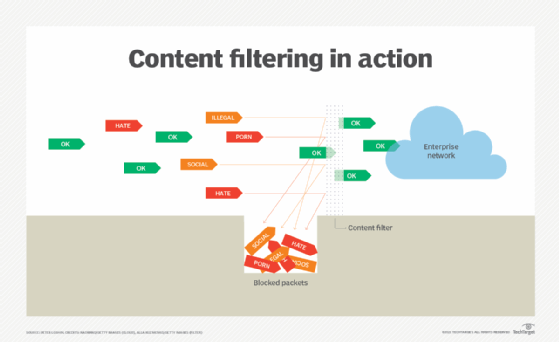
From a security perspective, filters are largely controlled by IT security administrators and security tool vendors. The purpose is to prevent access to certain digital assets, resources or locations that could pose a potential cyber threat if reached. Filters are put in place to protect a user's computing hardware, software and data from being hacked, stolen, manipulated or destroyed.
How are filters used in telecommunications?
In telecommunications, a filter -- such as one used for a digital subscriber line -- is a physical hardware device that's placed between the plain old telephone service network and customer DSL modem. The filter selectively sorts signals and passes through a desired range of signals, while suppressing the others. This kind of filter is used to suppress noise or to separate signals into bandwidth channels.
Placing the filter in front of the modem prevents interference from reaching the modem. Failure to do so can cause data transport performance issues on the connection. Additionally, a DSL filter is used to separate signals into bandwidth channels for improved quality of service.
How are filters used in multimedia editing tools?
In multimedia applications, a filter is a particular effect that can be applied to an image or part of a video clip or audio track. Many smartphone photo, video and social media applications contain these types of editing software filters. The video and photo editing filters are used for a variety of purposes, including the following:
- reducing or eliminating imperfections;
- enhancing colors, brightness or contrast;
- balancing overall exposure; and
- manipulating images and video with various overlays.
What is the splinternet, and what factors are causing internet technology to fragment?
